In today’s interconnected world, the Internet of Things (IoT) has become an integral part of our daily lives. From smart homes to industrial automation, IoT devices have revolutionized the way we live and work. However, with the proliferation of IoT devices, there also comes an increased risk of security vulnerabilities.
Security Risks of IoT Devices
One of the biggest security challenges of IoT devices is their susceptibility to cyber attacks. Because many IoT devices are connected to the internet, they can be targeted by hackers looking to exploit vulnerabilities in their software or hardware. This can result in unauthorized access to sensitive data, surveillance, or even control over the devices themselves.
Another significant security risk is the lack of standardized security protocols across IoT devices. Many manufacturers prioritize ease of use and functionality over security, leading to devices with weak or nonexistent security measures. This can make it easier for hackers to gain access to IoT devices and compromise their data.
How to Address IoT Security Challenges
Despite these challenges, there are several steps that can be taken to enhance the security of IoT devices and mitigate the risks associated with them.
Implementing Encryption
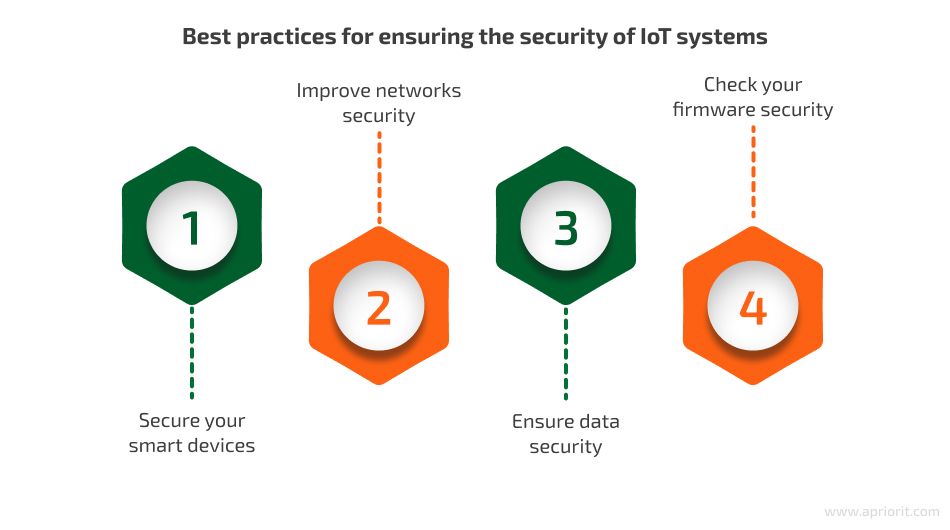
One of the most effective ways to secure IoT devices is to implement encryption. By encrypting data transmitted between devices and servers, manufacturers can ensure that sensitive information remains confidential and is not easily accessible to hackers. Strong encryption algorithms can help protect IoT devices from eavesdropping and data breaches.
Updating Firmware Regularly
Another important step in securing IoT devices is to regularly update their firmware. Manufacturers often release software updates that contain patches for known security vulnerabilities. By ensuring that IoT devices are running the latest firmware, users can protect themselves from potential cyber attacks and keep their devices secure.
Using Strong Passwords
Many IoT devices come with default passwords that are easy to guess or crack. To prevent unauthorized access, users should change these default passwords to strong, unique passwords that are difficult to guess. Additionally, users should avoid using the same password for multiple devices to minimize the risk of a widespread security breach.
Network Segmentation
Network segmentation is another effective strategy for securing IoT devices. By separating IoT devices from the main network, users can prevent hackers from gaining access to sensitive information or compromising other connected devices. This can help contain the impact of a potential breach and protect the overall security of the network.
Conclusion
While IoT devices offer numerous benefits and convenience, they also pose serious security risks that must be addressed. By implementing encryption, updating firmware regularly, using strong passwords, and implementing network segmentation, users can enhance the security of their IoT devices and protect themselves from potential cyber threats. It is essential for manufacturers, users, and cybersecurity professionals to work together to develop and implement robust security measures that will safeguard the integrity and confidentiality of IoT devices in an increasingly connected world.